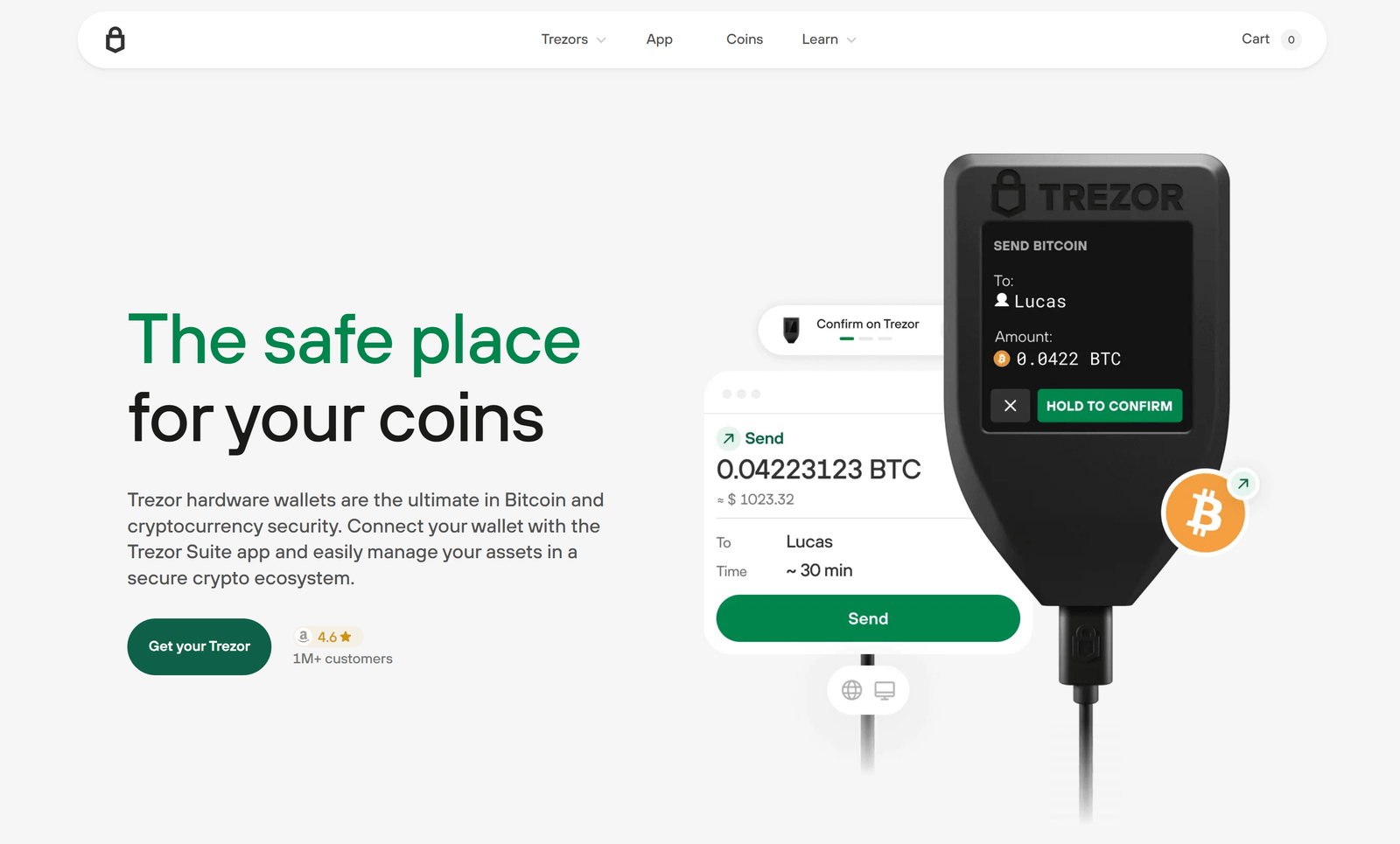
Trezor Hardware Wallet — Manage Your Crypto with Security
A clear, practical guide to using your Trezor hardware wallet to protect private keys, securely manage assets, and reduce online risk — written without any links and without exposing login passwords or sensitive credentials.
Trezor Hardware Wallet — Why choose one for secure crypto management?
Trezor hardware wallets are physical devices that keep your private keys isolated from the internet. By storing cryptographic keys on a dedicated device, a Trezor Hardware Wallet helps protect funds from common online threats like malware, phishing, and compromised computers.
- Private keys never leave the device — transactions are signed offline.
- Open design and transparent security model make auditing and trust easier.
- Pin protection and recovery seed reduce risk from device loss or theft.
Trezor Hardware Wallet — Unboxing and first steps (safe, no passwords)
When you receive your Trezor Hardware Wallet, inspect the packaging for tamper-evidence and factory seals. Power the device only when you are ready to set it up. During setup you will be guided to create a PIN and a recovery seed — both of which you must create and store securely. This guide does not request or display any PINs, passwords, or recovery words.
Trezor Hardware Wallet — Creating your PIN and recovery seed safely
Choose a PIN that you can remember but others cannot guess. The device will display the PIN-entry layout; you must enter the PIN using the on-device interface when requested. The recovery seed is a randomly generated list of words shown on the device screen — write them down on the provided recovery card or another secure, offline medium.
- Write the recovery seed on paper and store it in a safe location (e.g., a safe or secure deposit box).
- Consider using a metal backup plate for extra durability against fire and water.
- Do not store the recovery seed digitally (no photos, no cloud, no text files).
Trezor Hardware Wallet — Day-to-day usage and best practices
For routine operations, connect your Trezor Hardware Wallet to your computer or mobile device when you need to sign transactions. Always verify the transaction details on the device screen before approving. Use strong, unique passwords for any companion software accounts you control, but never use your device PIN or recovery words as those passwords.
- Verify recipient addresses and amounts directly on the device.
- Keep firmware updated — updates improve security and features.
- Use separate wallets for large long-term holdings and smaller daily-use wallets.
Trezor Hardware Wallet — Firmware and security updates
Keeping your Trezor Hardware Wallet firmware current is a key part of maintaining security. Firmware updates are applied on the device; verify update prompts on the device screen and confirm only when you initiated the update. Never accept an unsolicited firmware update from unknown sources.
Trezor Hardware Wallet — Recovering access if your device is lost or stolen
If your Trezor Hardware Wallet is lost or stolen, you can restore access to your funds using the recovery seed on another compatible hardware device or during a trusted restore process. Keep your recovery seed physically secure — that single paper (or metal backup) is the ultimate key to your crypto.
- If you suspect your seed was exposed, move funds to a new wallet whose seed you generate and secure immediately.
- Do not disclose your seed to anyone offering help — legitimate support never asks for it.
Trezor Hardware Wallet — Troubleshooting basics
Common issues are often caused by cable/connectivity problems, expired batteries (if applicable), or outdated firmware. If the device behaves unexpectedly, power-cycle it and reconnect. For more advanced troubleshooting, rely on official support channels and documentation from the device manufacturer — remember, never enter your recovery seed into a website or share it with a support agent.
Trezor Hardware Wallet — Final recommendations for secure crypto management
Use the Trezor Hardware Wallet as part of a layered security plan: combine secure device storage, careful operational habits, strong passwords for companion software, and physically secure backups of your recovery seed. Regularly review your security posture and update firmware and companion apps as recommended — but never at the cost of exposing your seed or PIN.